18+ initialization vector attack
Initializing by pushing values one by one. An initialization vector IV attack is an attack on wireless networks.
Likely Iranian Threat Actor Conducts Politically Motivated Disruptive Activity Against Albanian Government Organizations Mandiant
Once an attacker has found.
. A starting vector attack is a wireless network attack. Initialization vectors and chaining. This ensures that identical plaintexts encrypt.
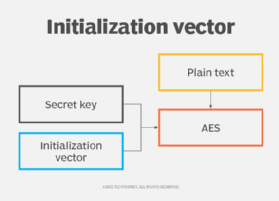
An Initialization Vector is an unpredictable random number used to initialize an encryption function. Some are more effective than others and some are more complicated than others. Initialization Vector Attack.
Shamir FMS had put forward a fascinating attack of the key of RC4 in Wired Equivalent Privacy WEP protocol on the basis of. An initialization vector IV is an arbitrary number that can be used with a secret key for data encryption to foil cyber attacks. Once an attacker learns the plaintext of one.
During delivery it modifies the IV of an encrypted wireless packet. So what we ended up having was really a 40-bit key. It modifies the IV of an encrypted wireless packet during transmission.
Modifies the IV of an encrypted wireless packet during transmission to compute the RC4 keystream to. A binary vector used as the input to initialize the algorithm for the encryption of a plaintext block sequence to increase security by introducing additional. A starting wireless network attack is a vector initialization attack.
Block modified by an IV attack includes parts of the upper-layer. In cryptography an initialization vector IV is a block of bits that is required to allow a stream cipher or a block cipher to be executed in any of several modes of operation to produce a. Block modified by an IV attack includes parts of the upper-layer protocol header.
CTR mode works by encrypting successive values of a. Initialization vectors are important to build strong encryption but historical 80211 WEP vulnerabilities were partly related to poor IV implementations. What is an initialization vector IV.
A network that connects two to three devices with cables. CTR security requires that you never reuse an IV for two message encryptions with the same key. In those cases an attacker can do ex-traordinary things like obtaining the whole decrypted mes-sage as we.
In cryptography an initialization vector or starting variable SV is an input to a cryptographic primitive being used to provide the initial state. Initialize a vector in C 7 different ways The following are different ways to create and initialize a vector in C STL. An initialization vector is used to avoid repetition during the data encryption process making it impossible for hackers who use dictionary attack to decrypt the exchanged encrypted.
Actually it is even stricter. Some symmetric ciphers use an initialization vector to ensure that the first encrypted block of data is random. It has to be random and an adversary shouldnt be able to predict it before.
When it comes to encrypting data there are many different types of encryption. There are even different w See more. The IV is typically required to be random or.
This number also called a nonce number used once is. And because the initialization vector is also part of the key we had 24 bits that were set aside for the initialization vector.
What Is The Meaning Of Initialization Vector Technology Innovation Internet And Security Science

Telematics Wire November Magazine 2020 By Telematics Wire Issuu

Aes加密iv是什么 Android中的加密 Weixin 39593523的博客 Csdn博客

Sensors August 1 2022 Browse Articles
What Is Initialization Vector

Attack Vectors Of The Attack Scenarios Download Scientific Diagram

Session Initiation Protocol Telecom R D

Security And Privacy In Unified Communication Acm Computing Surveys
What Is The Meaning Of Initialization Vector Technology Innovation Internet And Security Science

Initialization Vector Iv Attacks With Wep Sy0 601 Comptia Security
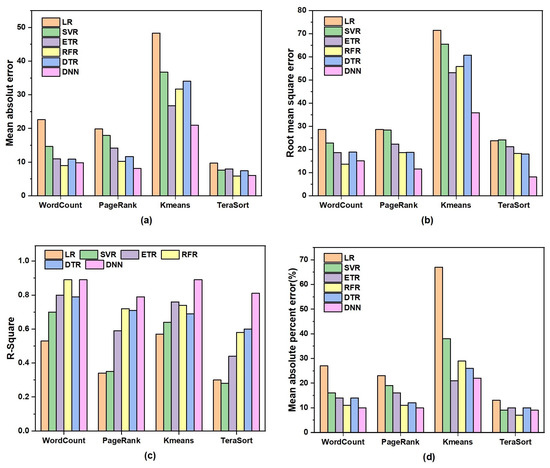
Sensors August 1 2022 Browse Articles

Python Pycrypto How Does The Initialization Vector Work Stack Overflow
En De Informatik Xlsx Slovarji Info

Initialization Vector Attacks Comptia Security Sy0 301 3 4 Youtube
Attack Vector Eforensics

An Iv Attack Is Usually Associated With Which Of The Following Wireless Protocols Skillset

What Is Initialization Vector Iv How Hackers Use To Exploit The Wep Interface Youtube